HI all,
I’m fairly new to Pulp. I just deployed Pulp via Docker Compose (Folders) and added SSL to the NGINX template.
Problem:
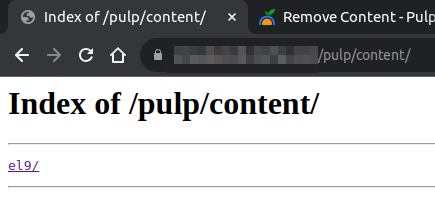
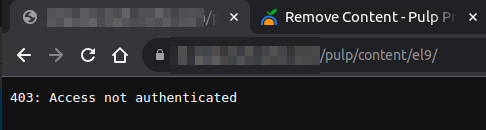
I created a repository called “el9” and added a package to it. After this I pulished the package to the repository and called it a day. I excpeted to see it inside /pulp/content/el9/. When I browse to /pulp/content/el9/ I get the error: 403: Access not authenticated. For my usecase it would be suitable that this content repository page is public. Is this even possible?
SECRET_KEY = "xxx"
CONTENT_ORIGIN = "http://pulp_content:24816"
DATABASES = {"default": {"HOST": "postgres", "ENGINE": "django.db.backends.postgresql", "NAME": "pulp", "USER": "pulp", "PASSWORD": "xxx", "PORT": "5432", "CONN_MAX_AGE": 0, "OPTIONS": {"sslmode": "prefer"}}}
CACHE_ENABLED = True
REDIS_HOST = "redis"
REDIS_PORT = 6379
REDIS_PASSWORD = ""
ANSIBLE_API_HOSTNAME = "http://pulp_api:24817"
ANSIBLE_CONTENT_HOSTNAME = "http://pulp_content:24816/pulp/content"
ALLOWED_IMPORT_PATHS = ["/tmp"]
ALLOWED_EXPORT_PATHS = ["/tmp"]
TOKEN_SERVER = "http://pulp_api:24817/token/"
TOKEN_AUTH_DISABLED = False
TOKEN_SIGNATURE_ALGORITHM = "ES256"
PUBLIC_KEY_PATH = "/etc/pulp/certs/public_key.pem"
PRIVATE_KEY_PATH = "/etc/pulp/certs/private_key.pem"
ANALYTICS = False
STATIC_ROOT = "/var/lib/operator/static/"
CSRF_TRUSTED_ORIGINS = ['https://xxx']
I also tried setting TOKEN_AUTH_DISABLED = True without any change. Trying to follow Token Authentication I already created keys and set them (see above) without any change.
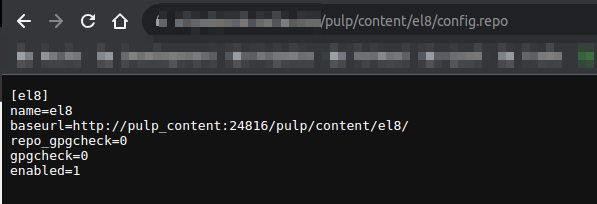
My NGINX Config looks like this
Config
error_log /dev/stdout info;
worker_processes 1;
events {
worker_connections 1024; # increase if you have lots of clients
accept_mutex off; # set to 'on' if nginx worker_processes > 1
}
http {
access_log /dev/stdout;
include mime.types;
# fallback in case we can't determine a type
default_type application/octet-stream;
sendfile on;
# If left at the default of 1024, nginx emits a warning about being unable
# to build optimal hash types.
types_hash_max_size 4096;
server {
listen 80 default_server;
server_name _;
return 301 https://$host$request_uri;
}
server {
# This logic enables us to have multiple servers, and check to see
# if they are scaled every 10 seconds.
# https://www.nginx.com/blog/dns-service-discovery-nginx-plus#domain-name-variable
# https://serverfault.com/a/821625/189494
resolver $NAMESERVER valid=10s;
set $pulp_api pulp_api;
set $pulp_content pulp_content;
# Gunicorn docs suggest the use of the "deferred" directive on Linux.
listen 443 default_server deferred ssl;
ssl_certificate /etc/pulp/certs/pulp_webserver.crt;
ssl_certificate_key /etc/pulp/certs/pulp_webserver.key;
ssl_session_cache shared:SSL:50m;
ssl_session_timeout 1d;
ssl_session_tickets off;
# intermediate configuration
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_prefer_server_ciphers on;
# HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months)
add_header Strict-Transport-Security max-age=15768000;
# If you have a domain name, this is where to add it
server_name xxx;
# The default client_max_body_size is 1m. Clients uploading
# files larger than this will need to chunk said files.
client_max_body_size 50m;
# Gunicorn docs suggest this value.
keepalive_timeout 5;
# static files that can change dynamically, or are needed for TLS
# purposes are served through the webserver.
root /opt/app-root/src;
location /pulp/content/ {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $http_host;
# we don't want nginx trying to do something clever with
# redirects, we set the Host: header above already.
proxy_redirect off;
proxy_pass http://$pulp_content:24816;
}
location /pulp/api/v3/ {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $http_host;
# we don't want nginx trying to do something clever with
# redirects, we set the Host: header above already.
proxy_redirect off;
proxy_pass http://$pulp_api:24817;
}
location /auth/login/ {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $http_host;
# we don't want nginx trying to do something clever with
# redirects, we set the Host: header above already.
proxy_redirect off;
proxy_pass http://$pulp_api:24817;
}
include /opt/app-root/etc/nginx.default.d/*.conf;
location / {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header Host $http_host;
# we don't want nginx trying to do something clever with
# redirects, we set the Host: header above already.
proxy_redirect off;
proxy_pass http://$pulp_api:24817;
# static files are served through whitenoise - http://whitenoise.evans.io/en/stable/
}
}
}
Am I missing something?
Expected outcome:
Either /pulp/content/* public or working token auth.
Pulpcore version:
3.47.0
Pulp plugins installed and their versions:
Summary
{
"versions": [
{
"component": "core",
"version": "3.47.0",
"package": "pulpcore",
"module": "pulpcore.app",
"domain_compatible": true
},
{
"component": "ansible",
"version": "0.21.2",
"package": "pulp-ansible",
"module": "pulp_ansible.app",
"domain_compatible": false
},
{
"component": "container",
"version": "2.18.0",
"package": "pulp-container",
"module": "pulp_container.app",
"domain_compatible": false
},
{
"component": "deb",
"version": "3.1.1",
"package": "pulp_deb",
"module": "pulp_deb.app",
"domain_compatible": false
},
{
"component": "maven",
"version": "0.8.0",
"package": "pulp-maven",
"module": "pulp_maven.app",
"domain_compatible": false
},
{
"component": "ostree",
"version": "2.3.0",
"package": "pulp-ostree",
"module": "pulp_ostree.app",
"domain_compatible": true
},
{
"component": "python",
"version": "3.11.0",
"package": "pulp-python",
"module": "pulp_python.app",
"domain_compatible": false
},
{
"component": "rpm",
"version": "3.25.1",
"package": "pulp-rpm",
"module": "pulp_rpm.app",
"domain_compatible": true
},
{
"component": "certguard",
"version": "3.47.0",
"package": "pulpcore",
"module": "pulp_certguard.app",
"domain_compatible": true
},
{
"component": "file",
"version": "3.47.0",
"package": "pulpcore",
"module": "pulp_file.app",
"domain_compatible": true
}
],
}
Operating system - distribution and version:
Rocky 9 with Docker Compose
Other relevant data:
N/A


 What API endpoints I would need to check if I have done it correctly?
What API endpoints I would need to check if I have done it correctly?