Problem:
Trying to authenticate through login throws out error
Pulpcore version:
3.29.1
Pulp plugins installed and their versions:
"versions": [
{
"component": "core",
"version": "3.29.1",
"package": "pulpcore",
"domain_compatible": true
},
{
"component": "ansible",
"version": "0.18.0",
"package": "pulp-ansible",
"domain_compatible": false
},
{
"component": "certguard",
"version": "1.6.5",
"package": "pulp-certguard",
"domain_compatible": true
},
{
"component": "container",
"version": "2.15.1",
"package": "pulp-container",
"domain_compatible": false
},
{
"component": "deb",
"version": "2.21.0",
"package": "pulp_deb",
"domain_compatible": false
},
{
"component": "file",
"version": "1.14.3",
"package": "pulp-file",
"domain_compatible": true
},
{
"component": "maven",
"version": "0.6.0",
"package": "pulp-maven",
"domain_compatible": false
},
{
"component": "ostree",
"version": "2.1.1",
"package": "pulp-ostree",
"domain_compatible": false
},
{
"component": "python",
"version": "3.10.0",
"package": "pulp-python",
"domain_compatible": false
},
{
"component": "rpm",
"version": "3.22.2",
"package": "pulp-rpm",
"domain_compatible": true
Operating system - distribution and version:
Pulp3 through Pulp Operator 1.0.0-alpha.8 ( latest version in the GitHub repo ) deployed in Kubernetes v1.25.6
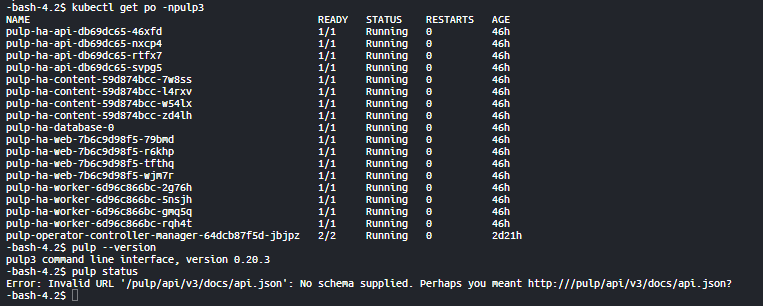
Other relevant data:
When trying to auth through log in I get thrown an error. Whenever i try to go to another path rather then /auth/login e.g. “/pulp/api/v3/artifacts” and I authenticate with the same credentials through that path then it works. Just wondering if something I did wrong led to this or is this a bug ?

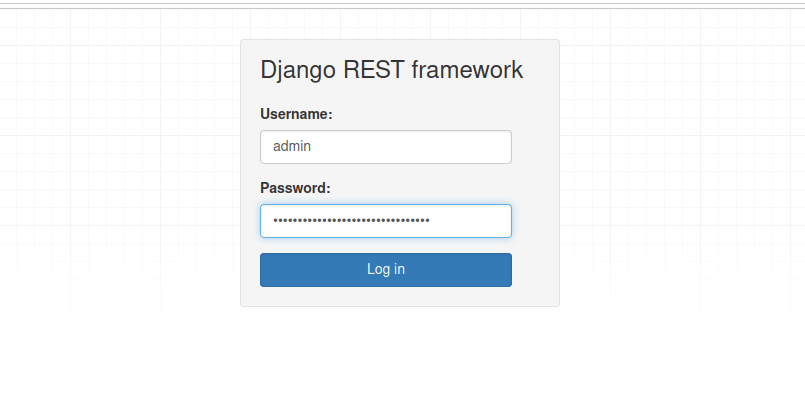

 Thanks for the correction Matthias!
Thanks for the correction Matthias!